
Due to the security challenges inherent when developing objects for the Internet of Things (IoT) as discussed in my previous article, the exploitation of IoT by hackers will be more and more common. IoT developers and companies, therefore, must make security arrangements paramount through all stages of their product's development.
In this article, I will define what we mean in the industry by a "security attack" and a "secure object," IoT security goals, and what are the most common forms of IoT attacks.
Traditional security goals are generally known as the "Confidentiality, Integrity, and Availability triad (CIA-triad)".
Confidentiality is a method in which only authorized people or objects can access sensitive data. With the advent of IoT, it is expected that multiple IoT objects might operate in sensitive environments such as hospitals, and hence the Confidentiality of such objects must be maintained.
Integrity, in the IoT context, involves maintaining the consistency, accuracy, and trustworthiness of data over its entire life cycle.
Availability ensures that IoT services, as well as applications, are always accessible by authorized objects or people.
In spite of the popularity of the CIA-traid, it fails to deal with new threats that may appear in a collaborative environment.
To cope with this issue, a comprehensive list of security goals, referred to as the "Information, Assurance, and Security (IAS) octave", has been proposed by two academics at the University of Cardiff, Yulia Cherdantseva and Jeremy Hilton.
The table below highlights the security goals introduced by the IAS-octave, along with their definitions associated with the IoT environment.
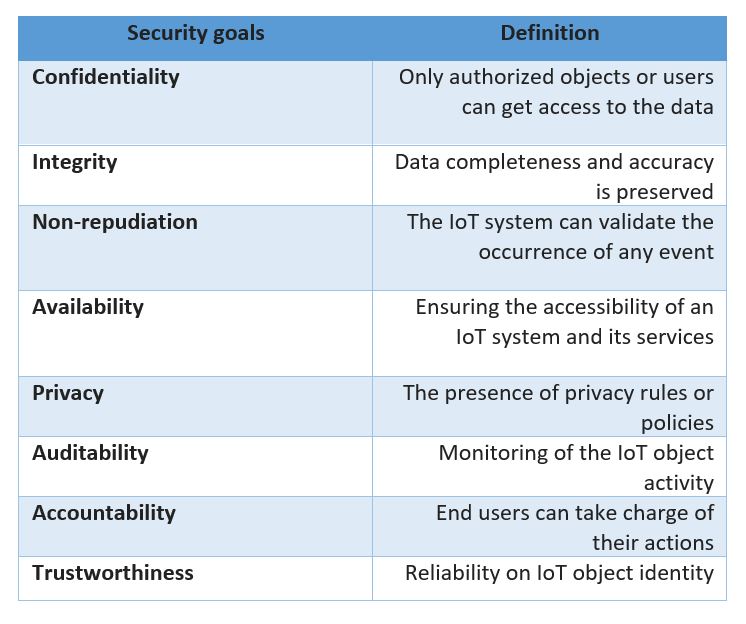
A table of the main IoT security goals
From the table, we can see that a secure object is an object that matches all the security goals, and a security attack is something that violates at least one of the security goals.
IoT applications may be vulnerable to multiple attacks, the most notable of which are:
Hardware Trojan: The Integrated Circuit (IC) is one of the main components of IoT objects. However, they are vulnerable to hardware "trojans" that maliciously alter an IC's configurations to allow hackers to exploit its functionalities and access software. The process of inserting a trojan into an IC takes place at its design phase by a malicious developer. There are two techniques in which the trojan can be activated. Either internally triggered (by monitoring one or more signals inside the IC) or externally-triggered (using a sensor or an antenna).
Object replication: This type of attack takes place by replicating an object's identification number in any IoT network leading to a huge drop in network performance since it might corrupt the packets and misdirect them.
Denial of Service (DoS) attacks: DoS attacks in IoT objects can be categorized into two groups: sleep deprivation and outage attacks.
2. Outage attacks: This kind of attack happens when an IoT object can no longer perform its main function due to sleep deprivation, unwanted error in the manufacturing stage, and code injection. Injecting Iran's nuclear system by Stuxnet was one of the most infamous attacks of this type. Stuxnet maliciously altered Iran's nuclear control system so that it could no longer discover unusual behavior, and prevented the system from shutting down in an emergency.
Physical attack: Some IoT objects may be deployed in remote environments and left unguarded. Having gained access to such objects, a hacker could extract security features, modify the operating system, and vandalize the circuits.
Malicious node: By gaining unauthorized access to IoT network as well as other objects, an adversary can add a malicious object to fully control the network by injecting false packets which hampers the delivery of valid messages.
Side-channel attack: As IoT objects execute their normal functions, it is possible that such objects may reveal sensitive information. This can take place even when these objects are not using wireless protocols to transmit data. An electromagnetic (EM) wave emitted by an object, for example, can offer valuable information about the state of the object. For example, a medical IoT object may unintentionally release sensitive information about the object as well as the patient.
Having addressed IoT attacks as well as security goals, the next article will highlight IoT countermeasures and illustrate their limitations. Furthermore, I will briefly introduce my novel methodology for securing IoT objects based on their security level certificates through which they will be able to communicate securely with each other or with the Internet.
Further reading:
The Internet of Risky Things by
Internet of Things: Security Challenges by
References:
Hezam, AA; Konstantas, D .; Nijdam, N. A Novel Methodology for Securing IoT Objects Based on their Security Level Certificates. Preprints 2020, 2020040362 (doi: 10.20944 / preprints202004.0362.v1).
Abdul-Ghani, HA; Konstantas, D. A Comprehensive Study of Security and Privacy Guidelines, Threats, and Countermeasures: An IoT Perspective. J. Sens. Actuator Netw. 2019 , 8 , 22.
Abdulghani, HA; Nijdam, NA; Collen, A .; Konstantas, D. A Study on Security and Privacy Guidelines, Countermeasures, Threats: IoT Data at Rest Perspective. Symmetry 2019 , 11 , 774.
Hezam Akram Abdul-Ghani, Dimitri Konstantas and Mohammed Mahyoub, “A Comprehensive IoT Attacks Survey based on a Building-blocked Reference Model” International Journal of Advanced Computer Science and Applications (ijacsa), 9 (3), 2018. http: // dx.doi.org/10.14569/IJACSA.2018.090349
Y. Cherdantseva and J. Hilton, “A Reference Model of Information Assurance & Security *.”
Image