
In this, the final of our three part series on entering the one percent of internet security, we will address the topic of Two Factor Authentication (known as 2FA) and using a Virtual Private Network, or VPN, to protect your identity. Despite being relatively less known than the good practices of creating strong passwords or using password managers, they are both easily accessible to the general public and, as with most things, only require a little application to incorporate them into daily habits of good internet security.
First off, Two Factor Authentication. 2FA is a second layer of security that is offered by many of the larger account services, such as Google, Twitter and Facebook. The implementation varies slightly, but the idea is the same – that the user has to confirm their identity using a second method of verification. This second layer can be in the form of a code sent via text message; a self-generated code in a specific app; or a grid of codes that are valid for a certain duration.
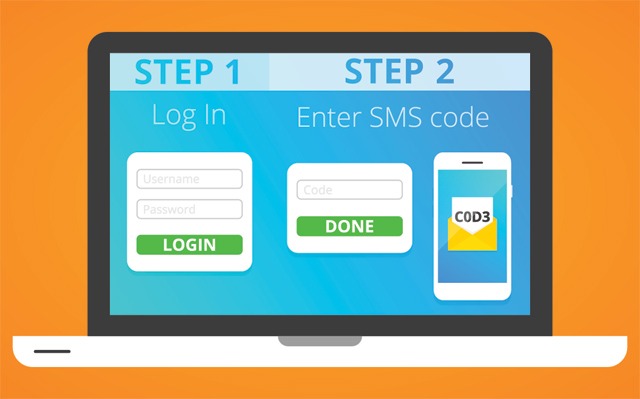
For example, Google uses an app called Google Authenticator. It can be used to provide a second layer of security with a number of compatible services, and they all work in the same way:
What it means is that each time you log into your account, you will need your user name and password as usual. But once you have entered your password, the account will prompt you to verify your identity by asking you for a code. This code is generated within the app which is on a scrolling timer, meaning that it expires every ninety seconds.
The advantage to this is that if your password is ever compromised, even someone who has your account details cannot access your account without physically having access to one of your trusted devices (where the authenticator app is installed).
This is an excellent system. Any account you request access to requires your express permission in order to open it. It also has the advantage, over systems such as text message based verification (where a code is sent to you via text message) that it will work in areas without an internet connection or phone signal, such as when travelling abroad.
Incidentally, the password manager, Lastpass, now also offers its own 2FA app or is compatible with Google Authenticator, adding an additional layer of security to your main vault of passwords.
Ah yes, this can pose a problem: if you lose your phone, are you locked out of all your accounts? The answer is no…provided you have set up the required safeguards. Again, it is a question of good practices. Most of the Authenticator services will ask for a back-up phone number in order to activate the service. This should not be your own phone number, but rather the number of someone whom you trust. In the event that your device is lost/stolen, then you will be able to retrieve access to your account via a text message code being sent to this backup number (the number should not be yours because for example, if your phone fell into a puddle of water and stopped working, then you won’t be able to receive any texts on it either).
Alternatively, it is possible to set up the authenticator app on two devices: a smartphone and a tablet for example; or a private phone and a work phone. Like this you always have a second available source of authentication if something goes wrong with your primary one.
In short, setting up 2FA where available will give you the strongest method of protecting your accounts. Even ignoring all the other good practices that have been discussed, if you are to continue using the same weak password across multiple sites, should an attacker gain access to your password then the Two Factor Authentication is the only thing that will protect your accounts and the information within.
The final point of discussion to touch upon is slightly more technical to understand, but simple in terms of its implementation (thanks to the fact that you as the user don’t actually do anything). These systems are called VPNs, or Virtual Private Networks.
A VPN is a subscription service that allows you to mask your identity online. This is useful if you are in an unsecured network (such as an internet café) where an unscrupulous individual may monitor traffic and be able to compromise your security. Without going into the details of it, a VPN creates a kind of “private tunnel” between yourself and what/who you’re connecting to, be that a site or a person. This tunnel renders the contents of what you are sending invisible to outside observers, meaning those people that you may be sharing a network with.
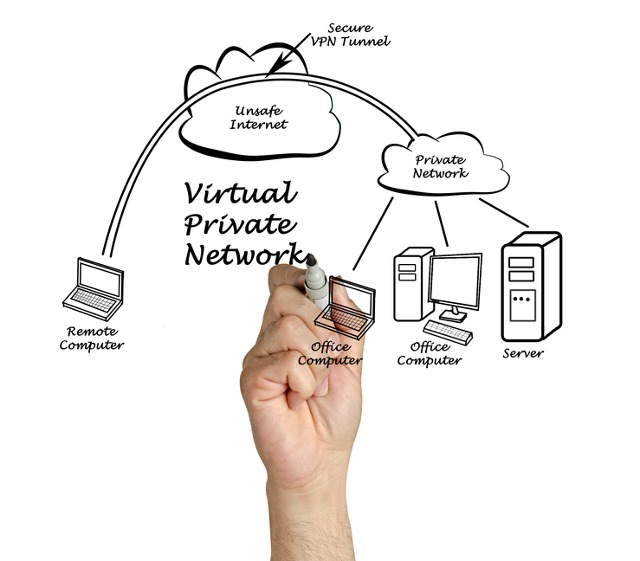
VPN Tunnel
Although this kind of anxiety about privacy may seem excessive, VPNs have proven invaluable for protecting individuals such as journalists and individuals in conflict zones or places with strict censorship laws, where they would be at risk of reprisal for their activity online. While this does not apply to most people, it is still an added facet of protecting your information from being compromised.
Sometimes, it is not even that the information has value to an attacker personally per se, but rather to the victim. If your account is compromised and you are locked out, regaining access may only be possible through paying a ransom to the attacker. In a worst case scenario, imagine being locked out of your email account: the security questions have been changed, thus the help center finds it impossible to identify you as the rightful owner. Email is the worst account to have compromised because it is usually possible to reset other account passwords by sending a “reset password” verification email to your personal email address. The fact that your account is not open to compromise can thus be a very reassuring thought.
Imagine being on a computer network that is NOT connected to the internet: this is a “private network”, where you can share information with other users physically connected to the network, but not with the wider world. The restriction to this is that while you do not have outside access, the advantage is that as access is limited to those who are physically present, there is a much greater degree of security. A VPN replicates this by essentially connecting you with your destination, as if you were on the same physical network while blocking out external traffic or observation.
As noted above, VPNs are subscription services. It means that you have to pay for a VPN service, and once enrolled, you will have access to its features. You install an app on your computer, smartphone or tablet, log in to the service, and from then on the VPN encrypts all information passing in and out of the device . You can find a list of VPN services and reviews here.
Although VPNs are designed to protect your privacy, bear in mind that you are subscribing to a service and entrusting that service with your information. This means that information that passes through them is liable to be seen. This is not wholly uncommon: after all, it’s what we do with the post office every time we send a letter – we expect our correspondence not to be read but once it leaves our hands it is really out of our control.
However, different VPN services have different policies regarding privacy, and who they are willing to turn information over to if asked. So it is worth doing a little research to find which company best corresponds to your specific needs. In short, a VPN service can give you much peace of mind especially when travelling and using multiple unsecured networks.
Sources:
http://www.pcadvisor.co.uk/how-to/internet/how-use-vpn-set-up-vpn-for-private-browsing-3466190/
https://www.bestvpn.com/best-vpn-services/
http://lifehacker.com/5935863/five-best-vpn-service-providers
http://lifehacker.com/how-to-boost-your-internet-security-with-dnscrypt-510386189
Photo credit : gn8 via iStockPhoto; vaeenma via iStockphoto