In a first article on cyber security, we discussed traditional forms of protecting our data on the internet. End-to-end encryption, or E2EE, is another method which is becoming a hot topic in the online world. There is not a single day when we do not see news about E2EE on IT Tech forums, the technology pages of the newspapers, or even at consumer gadget conferences. The launch of the first fully E2EE-capable mobile made waves on the net, and new e-mail services promising E2EE capability are cropping up every day.
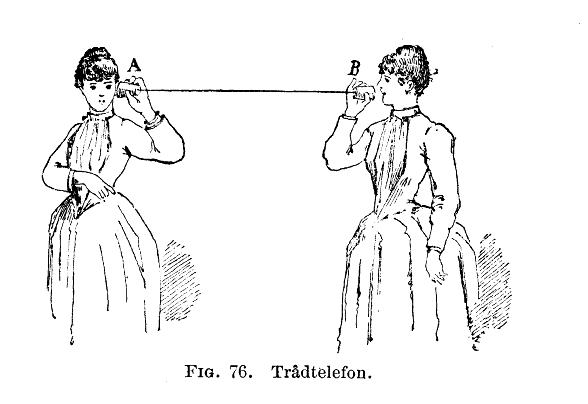
End-to-end encryption (E2EE) is a system of communication where only the communicating parties are able to read the messages. In other words, messages are encrypted in a way that only the unique recipient of a message is allowed to decrypt it, and not anyone in between. No “eavesdroppers” can access the cryptographic keys required to decrypt the conversation, including telecom and internet providers or the service provider who runs the messaging services. Because no third party has knowledge of the data being communicated or stored, surveillance or manipulation is impossible. Service provider’s servers act as illiterate messengers, only passing along the messages. For instance, companies using E2EE cannot hand over messages from their clients to the authorities.
In this case, the decryption key never leaves the user’s device. This concept might seem somehow paradoxal. If a service provider’s servers cannot see the key, how does it get onto the user’s device during the installation of the application in the first place?
The answer is simply another cryptographic technique known as public-key encryption. In public key crypto-systems, a software on a client’s device generates a pair of keys. One of them is called the “private” or “secret” key which is used for decrypting the message sent, and which never leaves sender’s device. The other one is the “public” key which is used for encrypting the messages received. It is designed in a way that only the corresponding private key can decrypt those messages. The public key can be shared with anyone who wants to encrypt a message with the sender.
Reactions to E2EE
As of today, common communication systems do not include E2EE. These systems can only guarantee the protection of communication traffic between client and server, not between the communicating parties themselves. Examples of non-E2EE messaging systems are Hotmail, Facebook, Google Talk, Yahoo Messenger. Dropbox and Google Drive are also examples of non-E2EE storage systems.
Despite E2EE’s absence in everyday use, the competition among tech companies has already begun, creating service offerings that promise better data protection with E2EE. Apple took the lead by announcing last year that its new iOS 8 operating system would encrypt nearly all data on IOS running devices by default, including text messages, photos and contacts. They also announced that the company would no longer be able to unlock client devices as long as they are password protected. Previous versions of the operating system were allowing Apple to unlock devices remotely. Then, Google made the announcement that they would do the same with their next Android software release.
The addition of E2EE to the services makes a slight but critical difference, because this means the company never sees the data or has any way of decrypting it. There is never a readable version of the messages on a server somewhere; if any public institution demands access, there is simply nothing in the hands of the company to hand over.
Of course, reactions to the E2EE from governments are not enthusiastic. FBI director James Comey called for tech companies offering end-to-end encryption to reconsider their business model. California State Assembly member Jim Cooper introduced a bill to prohibit the sale of smartphones with unbreakable E2EE encryption.
Meanwhile, the United Nations recently concluded that the use of encryption should be encouraged to protect freedom of expression.
Apple CEO Tim Cook was quite adamant about the fact that “any backdoor is a backdoor for everyone” and would weaken security for all. He also emphasized his support for the right of privacy: "History has shown us that sacrificing our right to privacy can have dire consequences…If those of us in positions of responsibility fail to do everything in our power to protect the right of privacy, we risk something far more valuable than money. We risk our way of life."
Anything else to consider regarding E2EE?
We could start thinking that E2EE is the ultimate solution to our security needs. However, that may not exactly be the case at the moment. E2EE has its own limitations. Users of E2EE (and also client-side encryption) can no longer use Big Data services offered by certain providers. For example, service providers like Gmail or Facebook, instead of just being a box that holds e-mail or other communication, provide other services as well. Gmail reviews the inbox and runs a spam filter to determine whether a given message is junk or spam. Gmail also indexes your email so you can quickly perform a search. It looks at an email’s content in order to understand its importance, and lets users create filters that automatically perform actions based on the content. All of these features rely on having access to, and being able to understand, your e-mail. Therefore many online features depend on the service provider accessing to your data. However, we can rest assured that technology companies are already working to close those gaps, and will start providing fully-functional E2EE-powered services soon.
Finally, of course, there are still two vulnerable points left to discuss: the two ends. Each user’s computer can still be attacked and/or hacked, and the perpetrator can steal the cryptographic key or simply read the recipients’ decrypted messages. Even the most perfectly-encrypted communication system is only as secure as the sender’s and receiver’s mailboxes on each end.
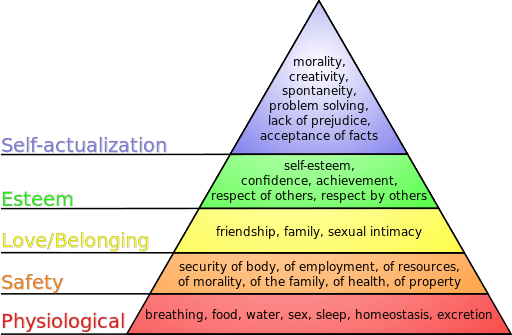 Maslow's famous hierarchy of needs pyramid places security just after the physiological basic needs of food and water. The need for security, still, comes before the needs for belonging and love, esteem, self-actualization and self-transcendence.
Maslow's famous hierarchy of needs pyramid places security just after the physiological basic needs of food and water. The need for security, still, comes before the needs for belonging and love, esteem, self-actualization and self-transcendence.
The internet eventually became an indispensable part of our lives. It is an essential tool that actually carries out tasks that help us to obtain some of the needs in Maslow’s pyramid. The security of the internet is therefore intrinsically linked with our own security requirements. It is certain that we will still be concerned with internet security, even as the internet continues to permeate our lives.
Sources:
https://en.wikipedia.org/wiki/End-to-end_encryption
http://searchsecurity.techtarget.com/definition/end-to-end-encryption-E2EE
http://www.wired.com/2014/11/hacker-lexicon-end-to-end-encryption/
http://secushare.org/end2end
http://www.howtogeek.com/166507/why-most-web-services-dont-use-end-to-end-encryption/
http://feelthebern.org/bernie-sanders-on-privacy-and-digital-rights/
https://support.1password.com/end-to-end-encryption/
http://www.howtogeek.com/166507/why-most-web-services-dont-use-end-to-end-encryption/
http://polyarista.tripod.com/
Image credits:
Public Domain, https://commons.wikimedia.org/w/index.php?curid=472708
J. Finkelstein (Using Inkscape.) , via Wikimedia Commons